INTERPOL report shows alarming rate of cyberattacks during Covid-19
An INTERPOL assessment of the impact of Covid-19 on cybercrime has shown a significant target shift from individuals and small businesses to major corporations, governments and critical infrastructure.
With organizations and businesses rapidly deploying remote systems and networks to support staff working from home, criminals are also taking advantage of increased security vulnerabilities to steal data, generate profits and cause disruption.
In one four-month period (January to April) some 907,000 spam messages, 737 incidents related to malware and 48,000 malicious URLs – all related to Covid-19 – were detected by one of INTERPOL’s private sector partners.
“Cybercriminals are developing and boosting their attacks at an alarming pace, exploiting the fear and uncertainty caused by the unstable social and economic situation created by COVID-19,” said Jürgen Stock, INTERPOL Secretary General. “The increased online dependency for people around the world, is also creating new opportunities, with many businesses and individuals not ensuring their cyber defences are up to date.
“The report’s findings again underline the need for closer public-private sector cooperation if we are to effectively tackle the threat COVID-19 also poses to our cyber health,” he concluded.
Key findings highlighted by the INTERPOL assessment of the cybercrime landscape in relation to the COVID-19 pandemic include:
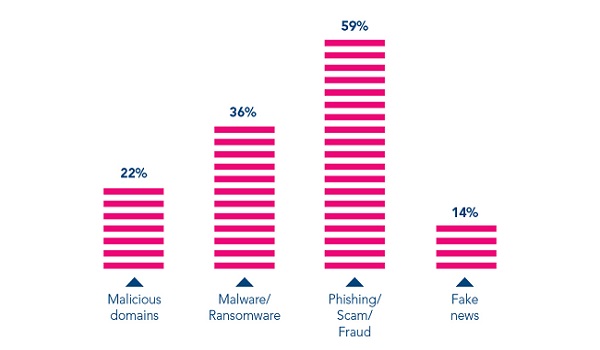
- Online Scams and Phishing: Threat actors have revised their usual online scams and phishing schemes. By deploying COVID-19 themed phishing emails, often impersonating government and health authorities, cybercriminals entice victims into providing their personal data and downloading malicious content.Around two-thirds of member countries which responded to the global cybercrime survey reported a significant use of COVID-19 themes for phishing and online fraud since the outbreak.
- Disruptive Malware (Ransomware and DDoS): Cybercriminals are increasingly using disruptive malware against critical infrastructure and healthcare institutions, due to the potential for high impact and financial benefit.In the first two weeks of April 2020, there was a spike in ransomware attacks by multiple threat groups which had been relatively dormant for the past few months.Law enforcement investigations show the majority of attackers estimated quite accurately the maximum amount of ransom they could demand from targeted organizations.
- Data Harvesting Malware: The deployment of data harvesting malware such as Remote Access Trojan, info stealers, spyware and banking Trojans by cybercriminals is on the rise. Using COVID-19 related information as a lure, threat actors infiltrate systems to compromise networks, steal data, divert money and build botnets.
- Malicious Domains: Taking advantage of the increased demand for medical supplies and information on COVID-19, there has been a significant increase of cybercriminals registering domain names containing keywords, such as “coronavirus” or “COVID”. These fraudulent websites underpin a wide variety of malicious activities including C2 servers, malware deployment and phishing.From February to March 2020, a 569 per cent growth in malicious registrations, including malware and phishing and a 788 per cent growth in high-risk registrations were detected and reported to INTERPOL by a private sector partner.
- Misinformation: An increasing amount of misinformation and fake news is spreading rapidly among the public. Unverified information, inadequately understood threats, and conspiracy theories have contributed to anxiety in communities and in some cases facilitated the execution of cyberattacks.Nearly 30 per cent of countries which responded to the global cybercrime survey confirmed the circulation of false information related to COVID-19. Within a one-month period, one country reported 290 postings with the majority containing concealed malware. There are also reports of misinformation being linked to the illegal trade of fraudulent medical commodities.Other cases of misinformation involved scams via mobile text-messages containing ‘too good to be true’ offers such as free food, special benefits, or large discounts in supermarkets.